Int'l : +1(646) 600-5072 | query@kbvresearch.com
Int'l : +1(646) 600-5072 | query@kbvresearch.com
Published Date : 20-May-2024 |
Pages: 101 |
Formats: PDF |
The United States (US) Mobile Security Market size is expected to reach $8.2 Billion by 2030, rising at a market growth of 17.8% CAGR during the forecast period.
There is a growing need for robust solutions that can safeguard mobile devices and data against a diverse array of threats, as mobile security has emerged as a pivotal issue for both individuals and organizations. Recent developments in the US mobile security market have been shaped by several key trends and advancements that reflect the industry's dynamic nature. These developments have played a crucial role in shaping the market landscape and influencing the adoption of mobile security solutions across various sectors.
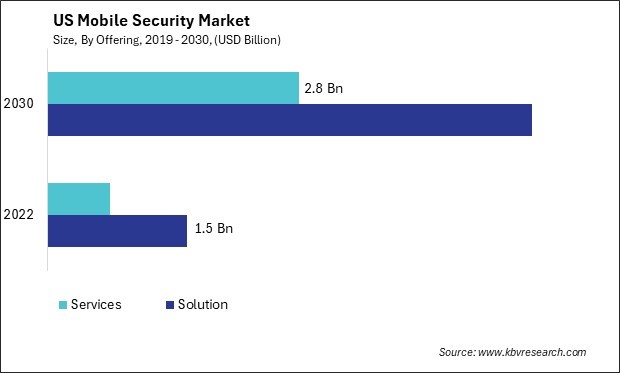
One of the notable recent developments in the US mobile security market is the increasing focus on comprehensive security solutions beyond traditional antivirus software. With the proliferation of mobile devices in both personal and professional settings, there has been a growing need for integrated security platforms to address multiple threat vectors, including malware, phishing attacks, device theft, and data breaches.
Another significant trend in the US mobile security market is emerging advanced technologies such as artificial intelligence (AI) and machine learning (ML) in mobile security solutions. These technologies are being leveraged to enhance threat detection capabilities, automate security processes, and provide real-time insights into potential security risks, enabling organizations to defend against evolving threats proactively.
The COVID-19 pandemic has significantly impacted the US mobile security market by accelerating the adoption of mobile devices for remote work, increasing vulnerabilities and threats targeting mobile endpoints, emphasizing the need for robust endpoint security measures, driving digital transformation initiatives, and highlighting compliance and privacy concerns related to mobile data. These factors have contributed to a heightened demand for comprehensive mobile security solutions to effectively address the evolving threat landscape and secure mobile devices in the post-pandemic era.
The United States has seen a notable rise in the demand for mobile application management (MAM) tools, driven by the increasing reliance on mobile applications for personal and professional use. A significant factor contributing to the increasing need for MAM tools in the United States is the pervasive integration of mobile devices within professional environments. As the number of personnel utilizing smartphones and tablets for professional obligations continues to rise, organizations strive to establish efficient mechanisms for overseeing and safeguarding the applications that are installed on these devices.
Furthermore, the rise of bring-your-own-device (BYOD) policies in the workplace has contributed to the increased demand for MAM solutions. When employees bring their own devices to work, IT departments face unique challenges in managing and securing corporate applications and data stored on these devices. MAM tools can separate personal and work-related apps and data on BYOD devices, ensuring corporate information remains secure without compromising the user experience.
Additionally, the demand for MAM tools has driven innovation in the mobile security market, developing more sophisticated and comprehensive security solutions. Vendors in the mobile security space have responded to the need for enhanced application management and security by integrating MAM capabilities into their offerings or developing specialized solutions that cater specifically to the requirements of application-centric security. Therefore, as the demand for MAM continues to grow, it is expected to further shape the evolution of the mobile security market, leading to the development of more advanced and integrated mobile security solutions tailored to the needs of modern enterprises.
The telecom and IT sector in the United States has experienced rapid expansion, driven by technological advancements, increasing demand for digital services, and the evolving needs of businesses and consumers. The sector has witnessed significant advancements in telecommunications infrastructure, cloud computing, data analytics, artificial intelligence (AI), and the Internet of Things (IoT). These technological innovations have enabled the development of new services, improved connectivity, and enhanced the efficiency of IT operations across various industries.
Furthermore, the increasing demand for digital services has played a crucial role in expanding the Telecom and IT sectors. The proliferation of smartphones, tablets, and other connected devices has led to a surge in data consumption and the need for high-speed connectivity. In response, investments have been made in network infrastructure, such as the implementation of 5G networks, in order to satisfy the increasing need for communication services that are both quicker and more dependable.
Additionally, the evolution of telecommunications infrastructure, including deploying advanced networks such as 5G, has led to increased connectivity and data transmission speeds. While these advancements have brought numerous benefits in improved communication and efficiency, they have also introduced new security challenges related to protecting sensitive data transmitted over these networks. This has driven the need for mobile security solutions to safeguard data in transit and ensure secure communication channels.
Furthermore, the growing intricacy and refinement of mobile threats—such as phishing attacks, malware, and data breaches—have emphasized the criticality of sophisticated mobile security solutions that can immediately identify and counteract these risks. As cybercriminals continue to target mobile devices as lucrative attack vectors, the demand for proactive and adaptive mobile security solutions to counter these evolving threats effectively has grown. Hence, expanding this sector will promote the market's growth.

Numerous companies have positioned themselves as major players in the fiercely competitive US mobile security market by providing solutions for mobile security that address the evolving cybersecurity requirements of consumers and businesses. One of the prominent companies in the US mobile security market is Symantec Corporation, known for its comprehensive suite of cybersecurity products, including mobile security solutions that protect against threats targeting mobile devices. Symantec's mobile security offerings encompass app scanning, anti-malware protection, device encryption, and secure web browsing, catering to enterprise and individual users.
Another major player in the US mobile security market is McAfee, LLC, which offers various mobile security solutions to safeguard devices against malware, phishing attacks, and other mobile threats. McAfee's mobile security offerings include antivirus protection, secure VPN services, app privacy controls, and anti-theft features, addressing the diverse security needs of mobile users.
Cisco Systems, Inc. is also a significant player in the US mobile security market, offering a portfolio of mobile security solutions focusing on threat detection, network security, and device management. Cisco's mobile security offerings leverage its expertise in network security to provide comprehensive protection for mobile devices and data, particularly in enterprise environments with complex IT infrastructures.
Furthermore, Lookout, Inc. has established itself as a leading provider of mobile security solutions in the US, specializing in mobile threat defense and securing mobile devices against advanced cyber threats. Lookout's mobile security platform offers features such as threat intelligence, mobile app analysis, and real-time threat detection, catering to organizations looking to secure their mobile fleets against sophisticated threats.
These companies, among others, have played a crucial role in shaping the US mobile security market, offering innovative solutions and services that address the growing challenges of mobile cybersecurity. As the mobile landscape continues evolving, these companies are expected to remain at the forefront of mobile security innovation, driving advancements and setting industry standards for best practices.
By Offering
By Operating System
By Deployment
By Enterprise Size
By Vertical